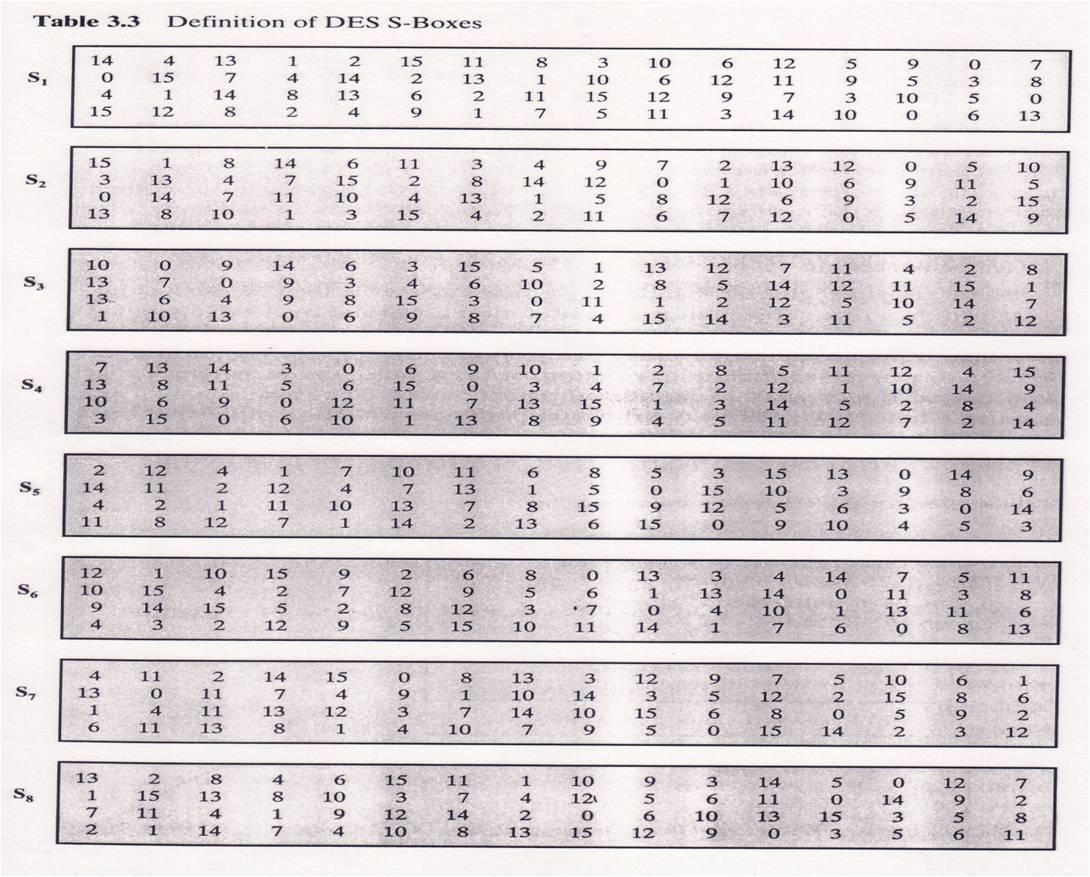
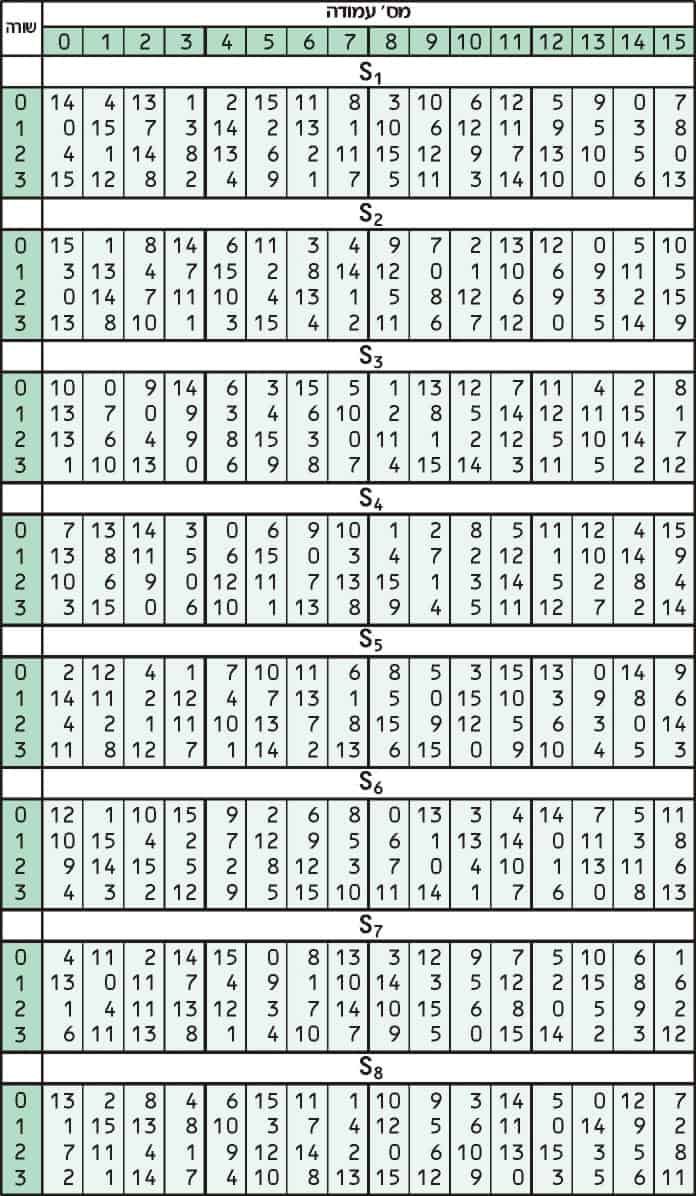
Function S-box S1 (in the DES algorithm) represented as a table and its... | Download Scientific Diagram

Inverse S-box: substitution values for the byte xy (in hexadecimal format). | Download Scientific Diagram

2c) In DES, if the 6-bit input to S-box S5 is 52 (in OCTAL), what is its output (in OCTAL)? - YouTube
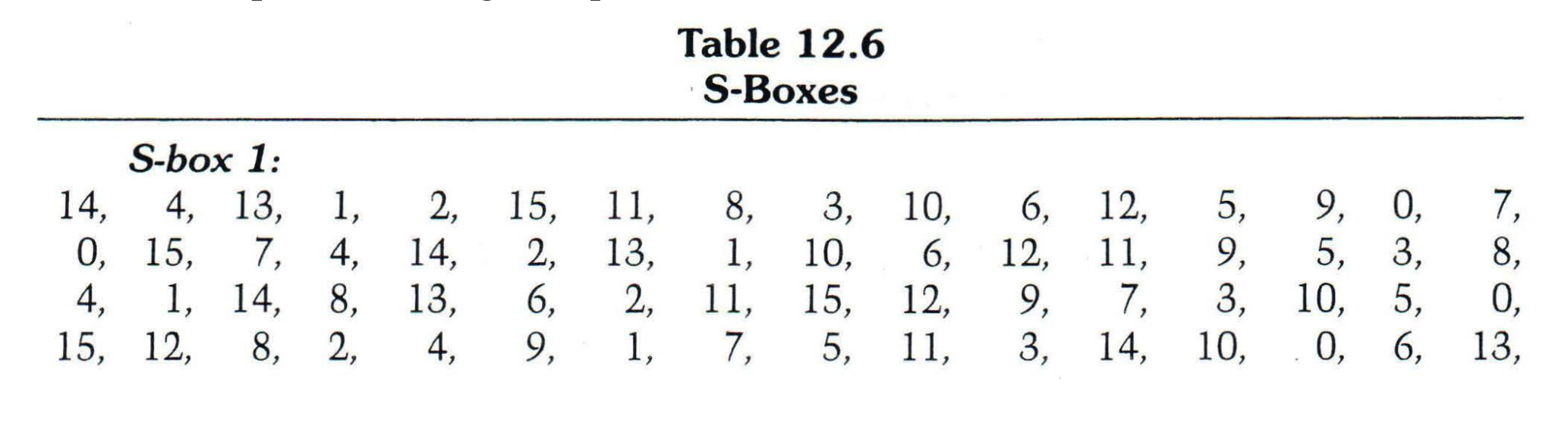
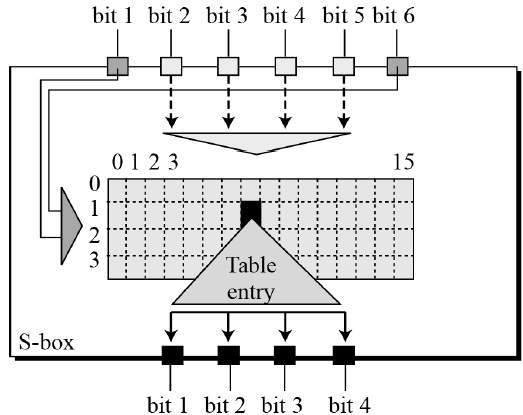
![9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book] 9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]](https://www.oreilly.com/library/view/computer-security-and/9780471947837/images/ch009-t004.jpg)
![PDF] S-box, SET, Match: A Toolbox for S-box Analysis | Semantic Scholar PDF] S-box, SET, Match: A Toolbox for S-box Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6a9f62c51d9fb0186bb2b9be304de24f69e19ffa/7-Table1-1.png)



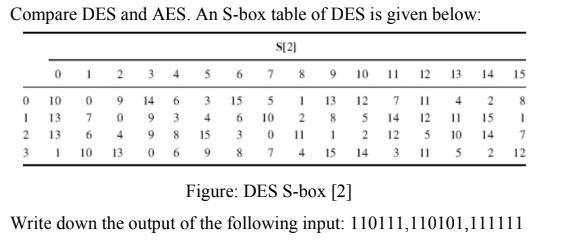





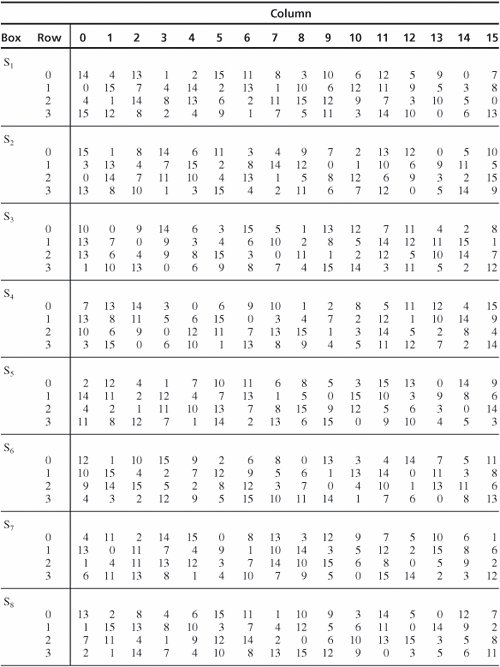




![PDF] Dynamic AES-128 with Key-Dependent S-box | Semantic Scholar PDF] Dynamic AES-128 with Key-Dependent S-box | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6d2516fa47f8a582e3fbf6ec971fd50a3c01ab7c/2-Table1-1.png)